VMware advised their vCenter users to update vCenter Server versions 6.5, 6.7, and 7.0 immediately, after a pair of vulnerabilities were reported privately to the company.
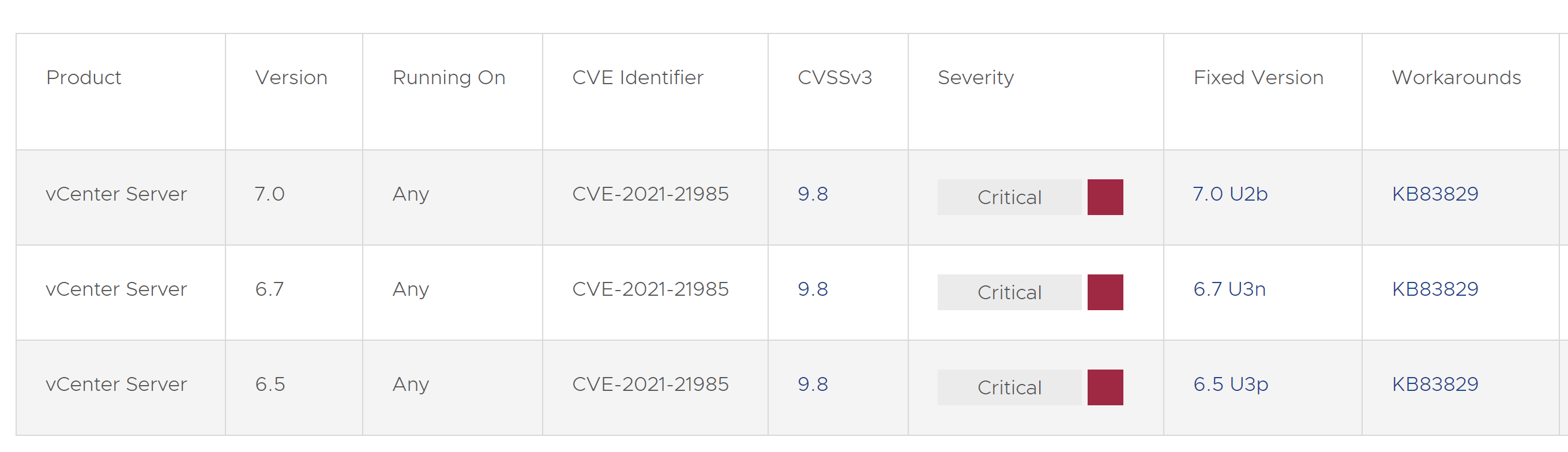
CVE-2021-21985 – remote code execution vulnerability in a vSAN plugin enabled by default in vCenter that an attacker could use to run whatever they wished on the underlying host machine, provided they can access port 443. Even if users do not use vSAN, they are likely to be affected because the vSAN plugin is enabled by default.
“The vSphere Client (HTML5) contains a remote code execution vulnerability due to lack of input validation in the Virtual SAN Health Check plug-in which is enabled by default in vCenter Server,”
A malicious actor with network access to port 443 may exploit this issue to execute commands with unrestricted privileges on the underlying operating system that hosts vCenter Server.
Impacted Products
- VMware vCenter Server (vCenter Server)
- VMware Cloud Foundation (Cloud Foundation)
How to Fix (Resolution) – Apply Patches
VMware has released patches that address a new critical security advisory, VMSA-2021-0010 (CVE-2021-21985 & CVE-2021-21986). This needs your immediate attention if you are using the vCenter Server.
Upgrade vCenter 7.0 -> vCenter 7.0 U2b
Upgrade vCenter 6.7 -> vCenter 6.7 U3n
Upgrade vCenter 6.5 -> vCenter 6.5 U3p
How to apply the Patch to the vCenter Server
Since we no more have windows based vCenter from vSphere 7.0, Let’s concentrate only on appliance based vCenter server here. We have to apply the patch to the vCenter server via the vCenter Server VAMI page (https://<vcenter-ip or name>:5480).
There are two ways to apply the pacth via the VAMI page.
vCenter Server with Internet Connectivity
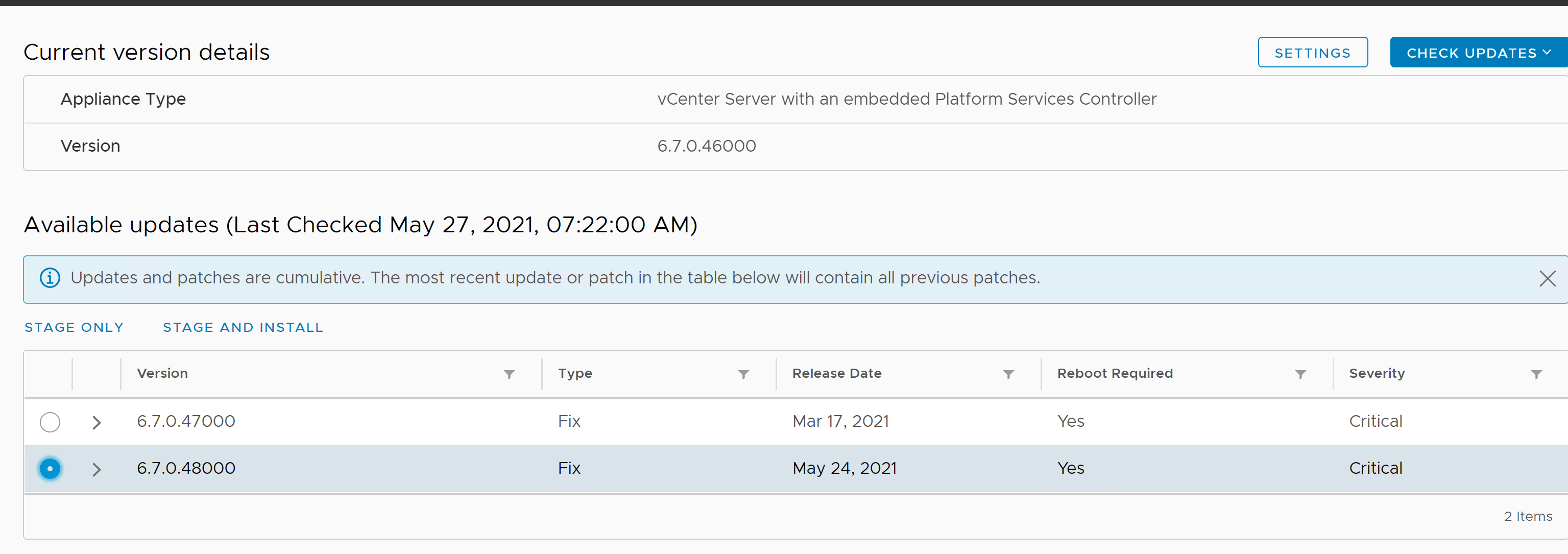
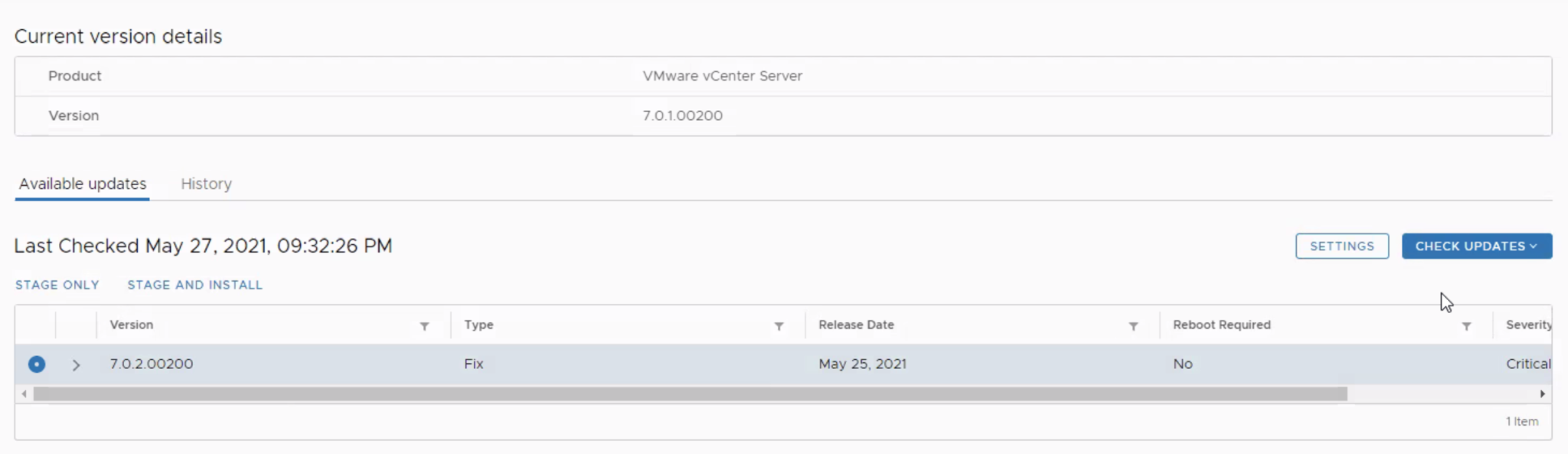
If your vCenter is having internet connectivity, It will automatically show the available patches for the vCenter server.
Select the patch -> Click Stage and Install
vCenter without internet Connectivity
For offline upgrade, Download the vCSA appliance Upgrade ISO and attach it to the vCenter Server Appliance virtual machine.
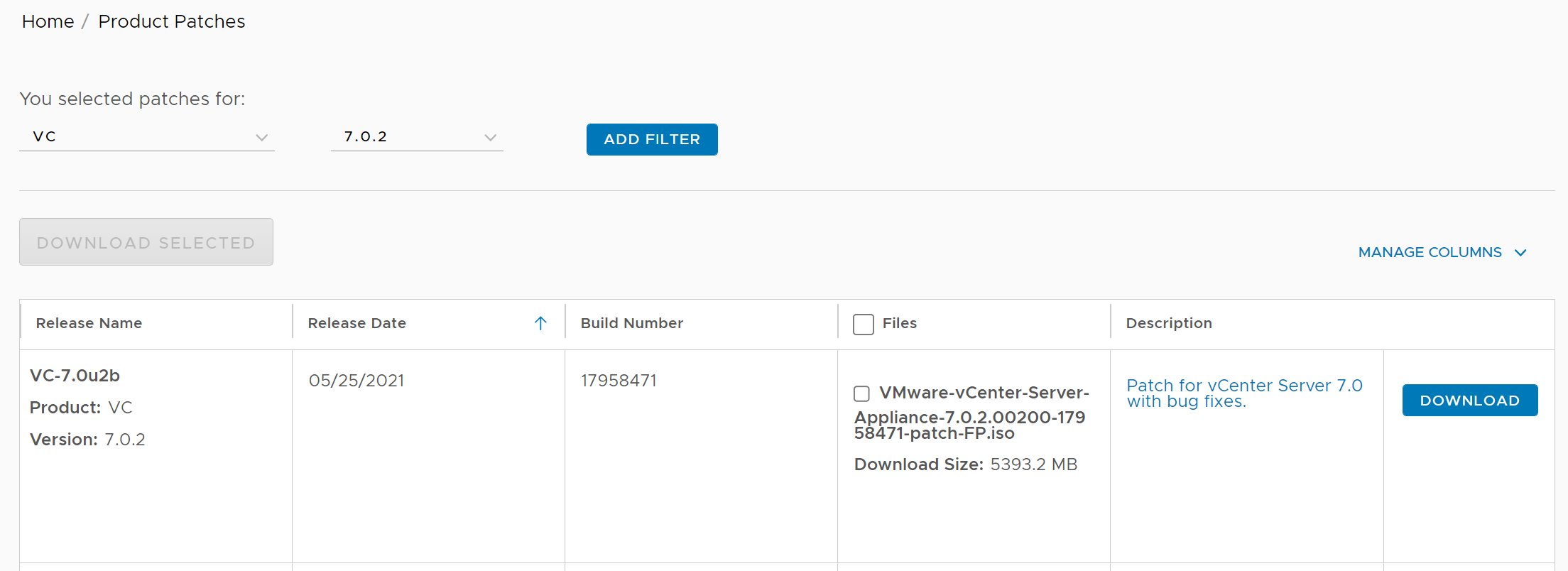
How to download the Upgrade ISO
Go to -> VMware Patch download Page and log in with your my vmware credentials. Select VC from the Select a Product drop-down menu. Select the appropriate version based on your vCenter version and download the patch.
Make sure the “Connected” checkbox is selected and click on Ok. Before performing the Upgrade, I always recommend taking a snapshot of your vCSA appliance.
Log in to the vCenter Server appliance VAMI page using the URL (https://vCenter-appliance-name:5480) and log in with the root credentials.
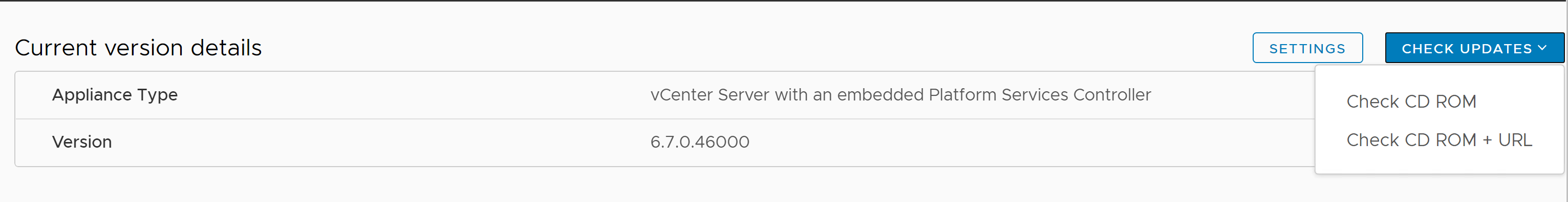
In the vCenter Server Appliance management, Click on Update. You can check the current version of the vCenter Server appliance and build details. Click on Check Updates – > Check CDROM for offline Upgrade
Select the Patch and Click Stage and Install.
It will restart the vCenter server if needed. The patch is successfully installed.
Workaround:
VMware has investigated these issues and has determined that the possibility of exploitation can be removed via disablement of impacted plugins by performing the steps detailed in the KB Article https://kb.vmware.com/s/article/83829
I hope this article gives the entire details about this vCenter vulnerability and how to remediate this issue in detail. I hope this is informative for you. Thanks for reading!!!. Be social and share it with social media, if you feel; worth sharing it.