Today, online security and privacy threats have become stronger and more prevalent than ever. We hear news about security breaches and virus attacks every now and then which is why more and more people have started learning about good security habits and take measures like using antivirus programs, firewalls, and free VPNs. However, if your data is extremely sensitive or if you don’t want to take any chances with your online identity and information, then you can achieve the ultimate level of anonymity by combining Tor, virtual machines (VMs), and VPNs. That said, first things first:

Tor
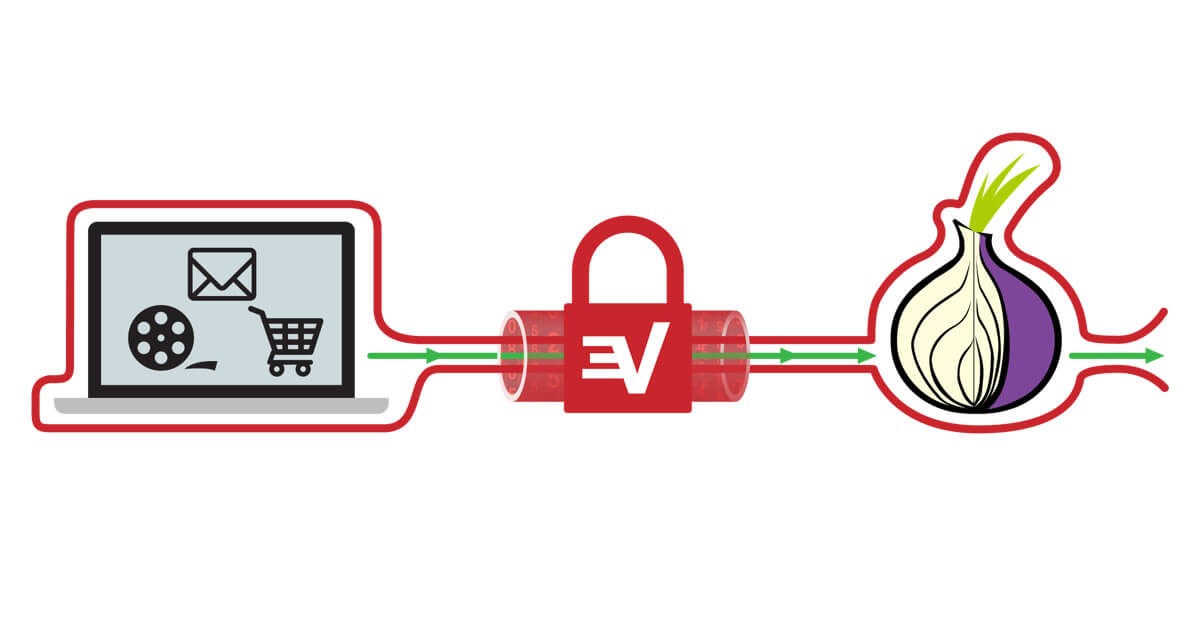
Tor Stands for The Onion Router which is a group of servers that allow you to surf the Internet without revealing your identity. When you use the service, then your information is transferred from one server to another and it’s also encrypted and decrypted during the entire process. So, even if someone tries to tap into your connection, they will only get to see the current router that you are on which can be any random one in the world.
You can use Tor browser to hide your identity and access your favorite websites without worrying about a cyber attack or data breach. The mechanism goes at great lengths to randomize your incoming and outgoing data packets to provide you the sense of security you seek.
Virtual Machine (VM)
A virtual machine can be considered as a computer system that runs on top of your existing computer system. It’s basically a software program that you can run on your computer in a way that all its resources like storage, processing power, RAM, etc. are sourced from the actual computer but the underlying processing and data are separated with the help of a software.
A VM allows you to protect yourself from online threats by hiding your hardware from outsiders as the hardware that the VM uses is emulated i.e. there are no dedicated RAM sticks, CPU, GPU, etc. Plus, in the worst-case scenario, if someone infects your VM, then your main computer is protected still. All you have to do is delete the virtual computer.
VMs are quite popular among businesses and tech-savvy users. Besides, there is a slew of free tools for VMware admins and others that one can use today which makes using VM technology easier.
VPN
VPN stands for virtual private network which is exactly what it sounds like- a virtual Internet network that you can use to surf different websites without revealing your true identity. This is because you get to go online through a server that’s located in a different location. Plus, the data that’s sent and received across a VPN connection is encrypted to add another layer of protection.
How to Combine all Three?
Combining VPN, VM, and Tor is not an easy task but it can greatly improve your online security. To achieve this feat, just follow these steps:
- Install a VM like Oracle VM VirtualBox (since it’s free)
- Install a VPN software and install on the virtual machine
- Install Tor Browser and launch it on the machine
To start using the system, take the following steps:
- Boot your virtual machine on your computer and wait until the OS is ready to use
- Launch the VPN application and connect to a secure server
- Launch the Tor browser once VPN is active and start accessing the Internet
- When you are done, you can shut down the system by closing the applications in the following order- Tor > VPN > VM.
So, there you have it- a guide on how to set up a computer system that has the ultimate level of security. Implementing it is easier than it sounds. Try it yourself today!