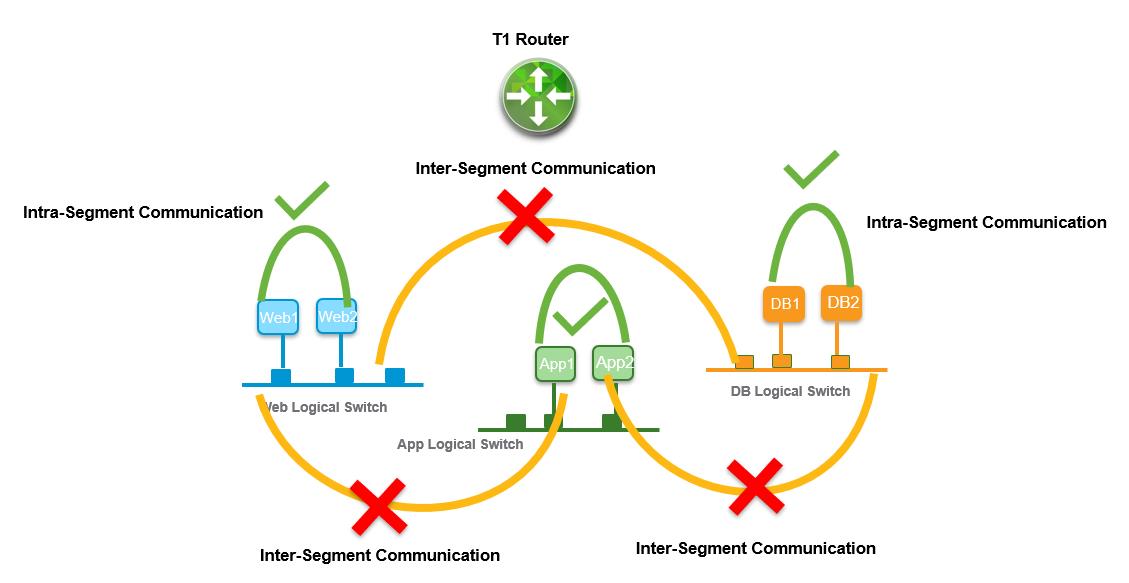
In our previous article, we have created multiple NSX-T Segments and also created NSX-T Tier 1 Gateway. As of now, VM’s connected to the same NSX-T segments can talk to each other but not able to talk to the VM’s in other segments. In the below example, We have a T1 router deployed. NSX-T segments created and also VM’s connected to the segments but we didn’t Connect NSX-T Segments with Tier-1 Gateway to enable routing between the VM’s in the different segments. How do we enable routing between VM’s in different segments?
Tier-1 routing layer interfaces with the logical switches defined by the tenant administrators, and provides a one-hop routing function between the NSX-T segments. So we need to connect NSX-T segments with Tier-1 gateway by creating gateway ports on the NSX-T segments. In this article, we will discuss details procedure to create Gateway ports on NSX-T segments to connect the NSX-T segments with the Tier-1 gateway to allow routing between the VM’s in different NSX-T segments.
How to Connect NSX-T Segments with Tier-1 Gateway
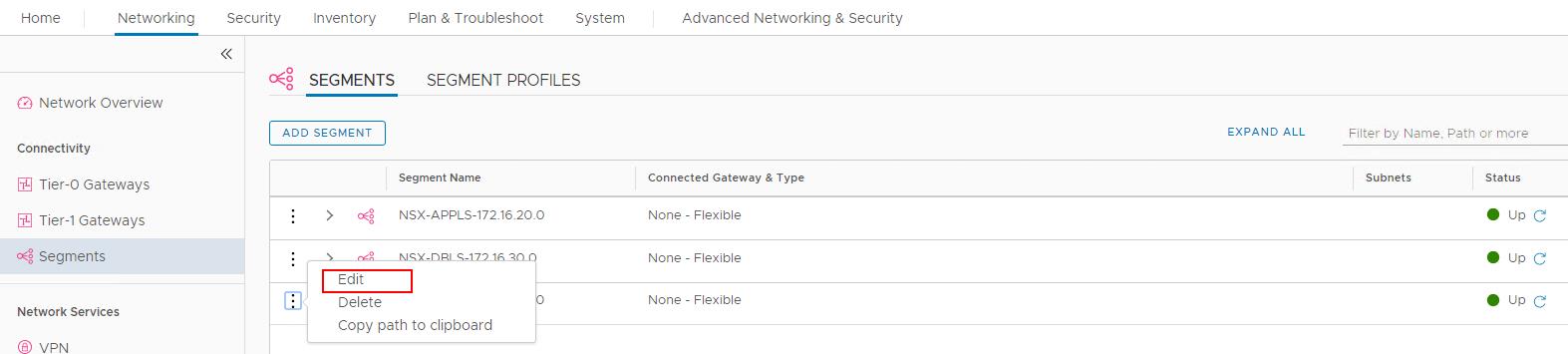
To Create Gateway ports in NSX-T segments, log in to NSX-T Manager with admin credentials. Click -> Networking -> Segements-> Select the Segments -> Click Edit
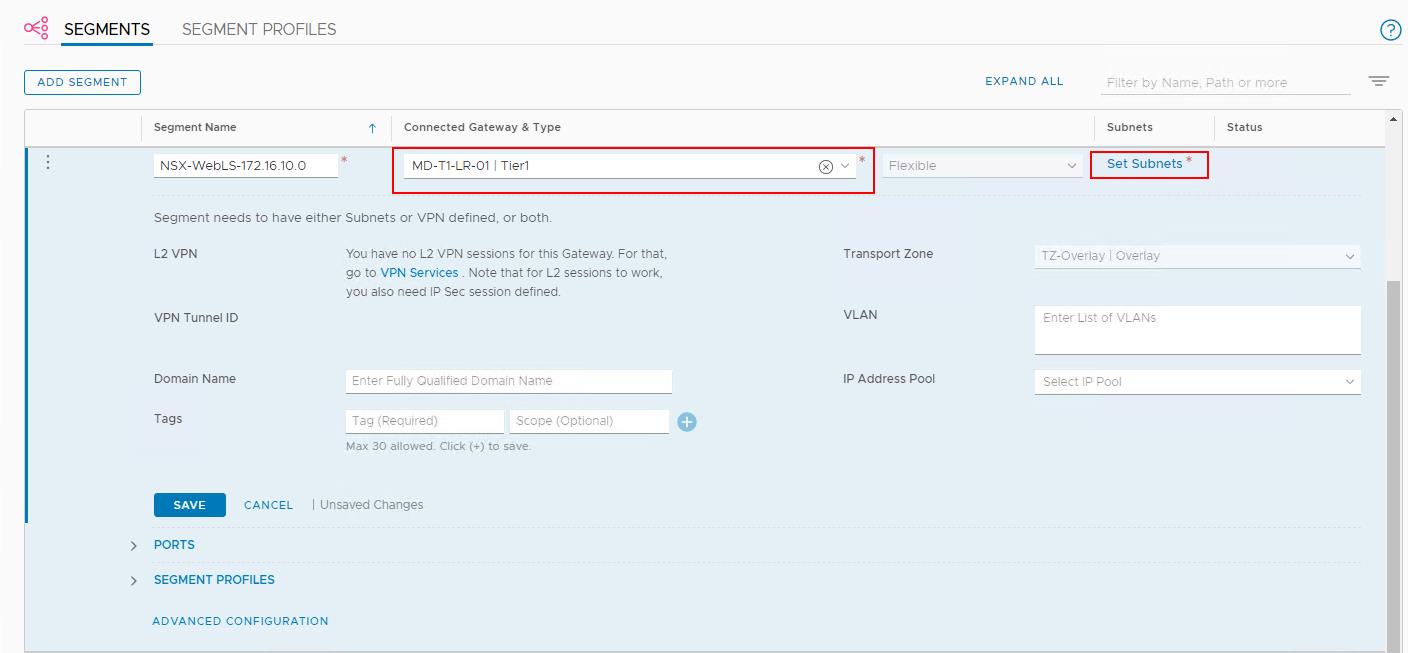
Select the Tier-1 Gateway “MD-T1-LR-01” from the “Connected Gateway & Type”. We have already created the Tier-1 gateway in our previous post.
Click on Set Subnets
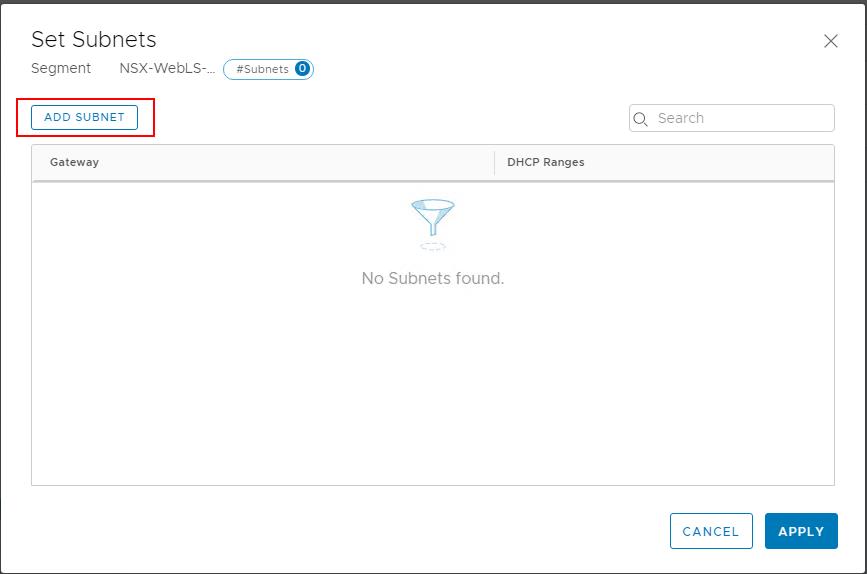
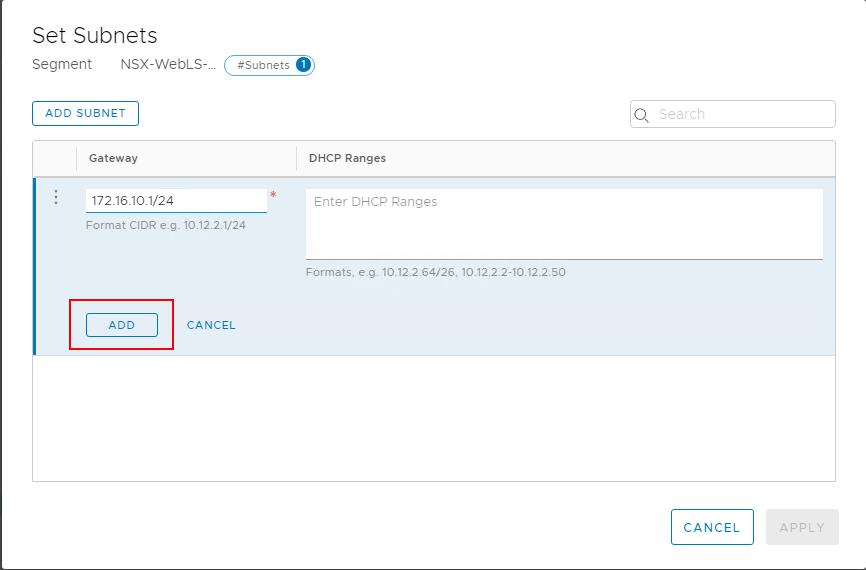
In the Set Subnets page -> Click ADD SUBNET
Enter the gateway address 172.16.10.1/24 in the Gateway field for segment “NSX-WEBLS-172.16.10.1” on the Set Subnets page. Click ADD.
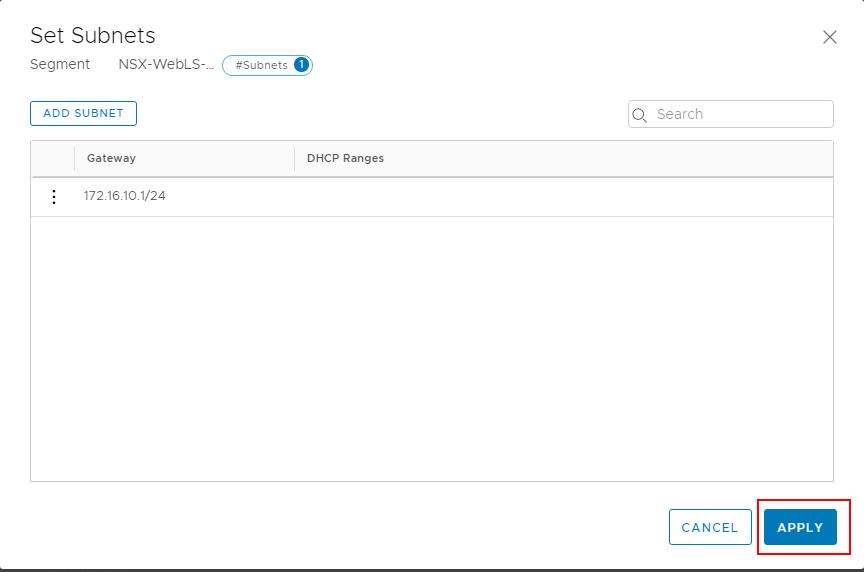
Click APPLY to set the gateway address for the subnet for the NSX-T segment.
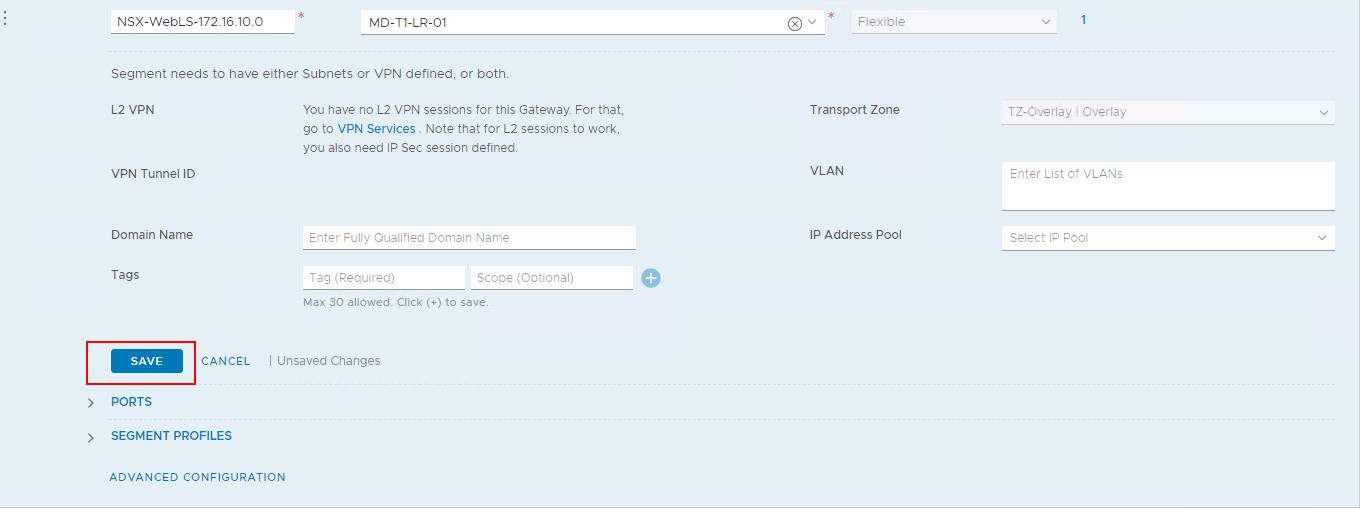
Click SAVE and click CLOSE EDITING.
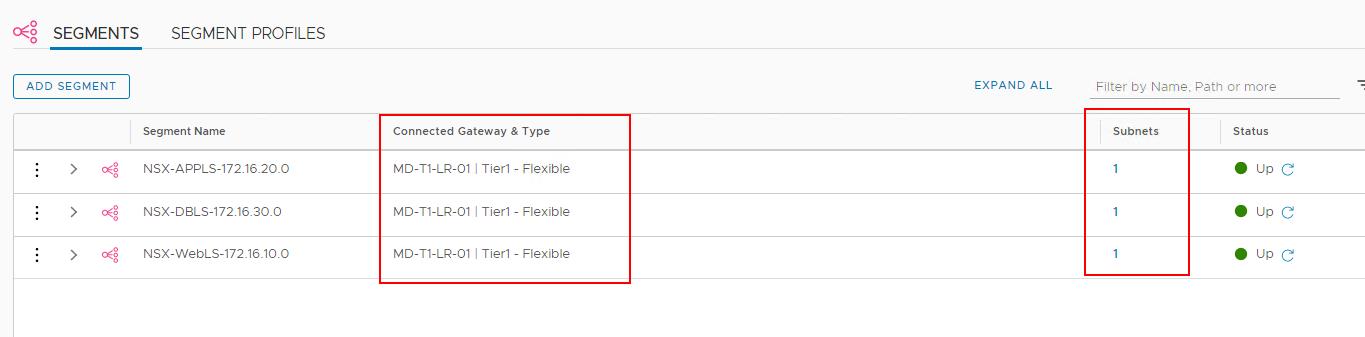
similarly, configure the gateway ports and set the subnets for all other NSX-T segments.
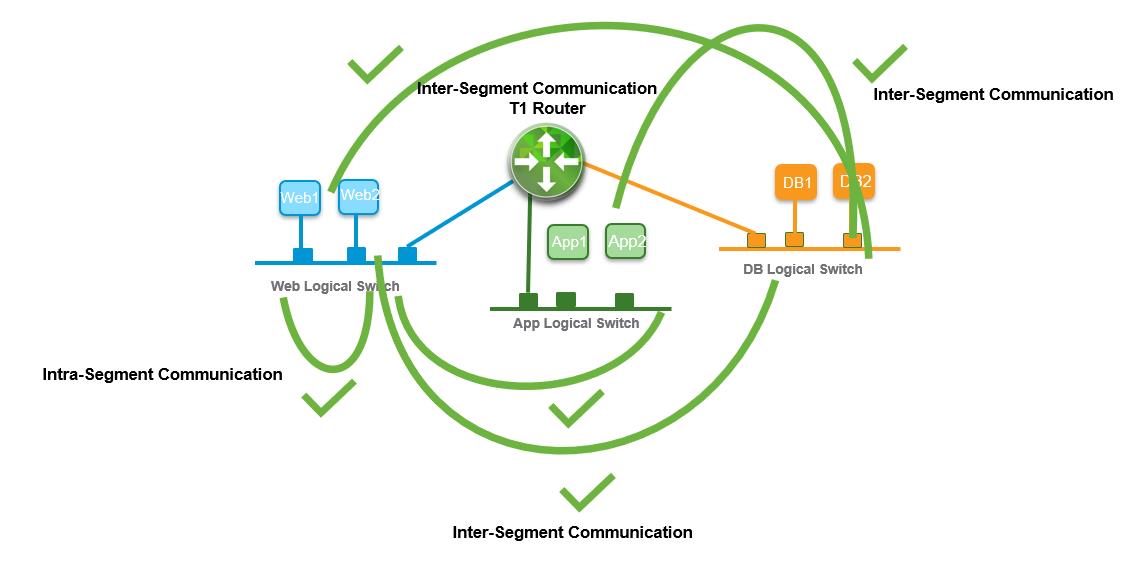
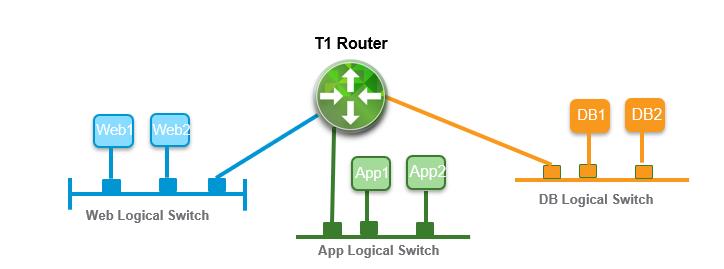
In the above steps, by creating a gateway port in each segment. we have connected NSX-T segments with Tier-1 gateway. Each of the segments is now directly connected to the Tier-1router. Tier-1 router provides east-west routing between the directly connected logical switches.
 Test East-West Connectivity
Test East-West Connectivity
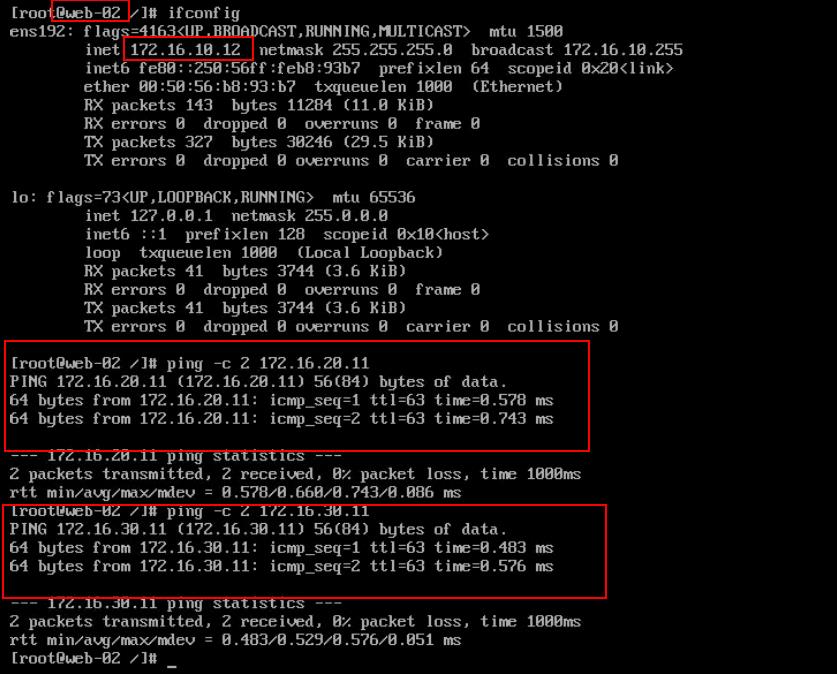
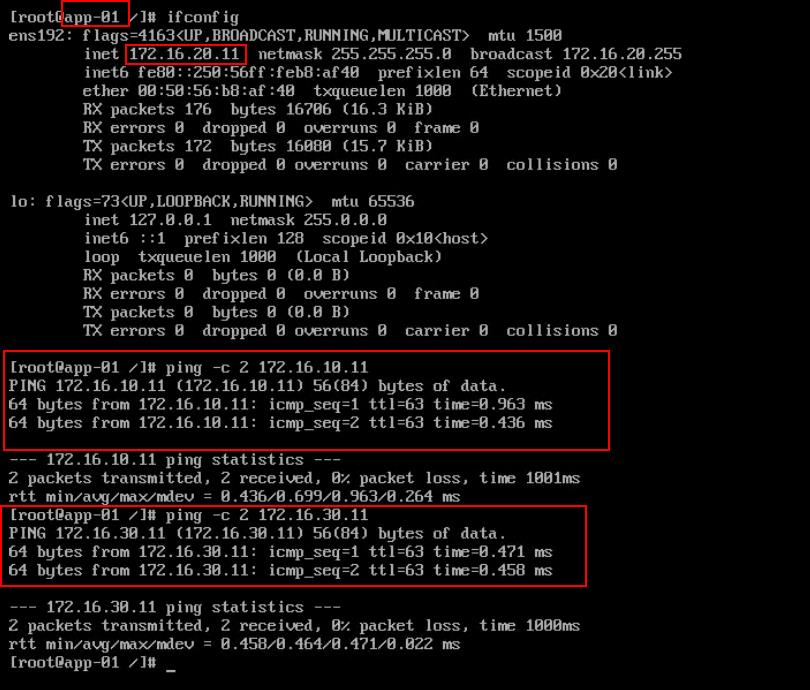
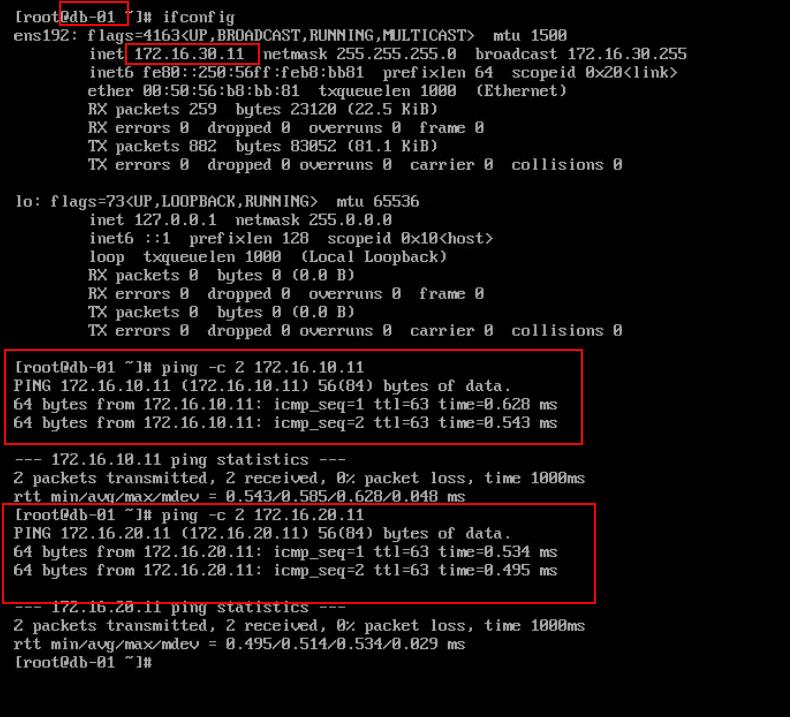
Below are the IP address of each of VM’s
Web-01 -> 172.16.10.11 (Connect to segment “NSX-WebLS-172.16.10.0”)
Web-02 -> 172.16.10.12 (Connect to segment “NSX-WebLS-172.16.10.0”)
App-01 -> 172.16.20.11 (Connect to segment “NSX-APPLS-172.16.20.0”)
DB-01 -> 172.16.30.11 (Connect to segment “NSX-DBLS-172.16.30.0”)
Ping Tests :
Ping between the virtual machine web-02 (172.16.10.11) and app-01 (172.16.20.11) connected in different segments is Successful
Ping between the virtual machine web-02 (172.16.10.11) and DB-01 (172.16.30.11) connected in different segments is Successful
Ping between the virtual machine app-01 (172.16.20.11) and web-01 (172.16.10.11) connected in different segments is Successful
Ping between the virtual machine app-01 (172.16.20.11) and DB-01 (172.16.30.11) connected in different segments is Successful
Ping between the virtual machine DB-01 (172.16.30.11) and web-01 (172.16.10.11) connected in different segments is Successful
Ping between the virtual machine DB-01 (172.16.30.11) and App-01 (172.16.20.11) connected in different segments is Successful
We have created the gateway ports in the segment to connect NSX-T Segments with the Tier-1 Gateway. Now we are able to ping and reach the virtual machines connected to different segments. Tier-1 router provides east-west connectivity between the segments connected directly. I hope this article is informative for you. Thanks for Reading!!!. Be social and share it with social media, if you feel worth sharing it.


 Test East-West Connectivity
Test East-West Connectivity