Capturing Networking Traffic is very important task when you run into Connectivity or network issues. We all are good at capturing network traffic in Guest OS level. What if you do when troubleshooting connectivity issues on your Virtulization enviornment. This post will help you to capture Network traffic on ESXi host using pktcap-uw tool.
The pktcap-uw tool is an enhanced packet capture and analysis tool that can be used in place of the legacy tcpdump-uw tool. The pktcap-uw tool is included by default in ESXi 5.5. This article provides information on using the pktcap-uw tool for packet capture and analysis.The tcpdump-uw tool can only capture packets/frames at the vmkernel interface level and cannot capture frames at the uplinks, or vSwitch, or virtual port levels. The new pktcap-uw tool allows traffic to be captured at all points within the hypervisor for greater flexibility and improved troubleshooting. It provides more options to capture the packets. Lets take a look how to use pktcap-uw tool to capture the network traffic.
Get help and Syntax information:
pktcap-uw -h |more
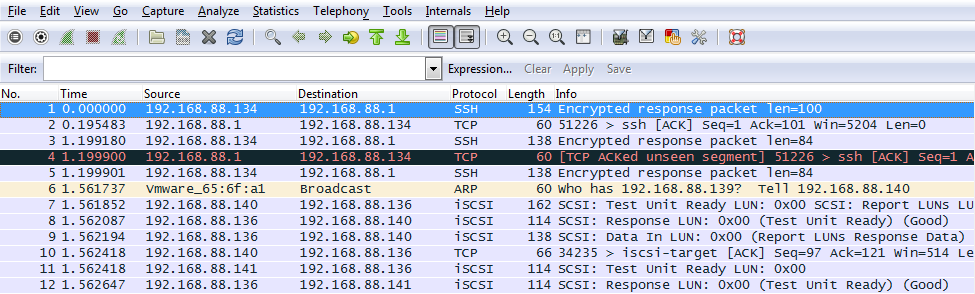
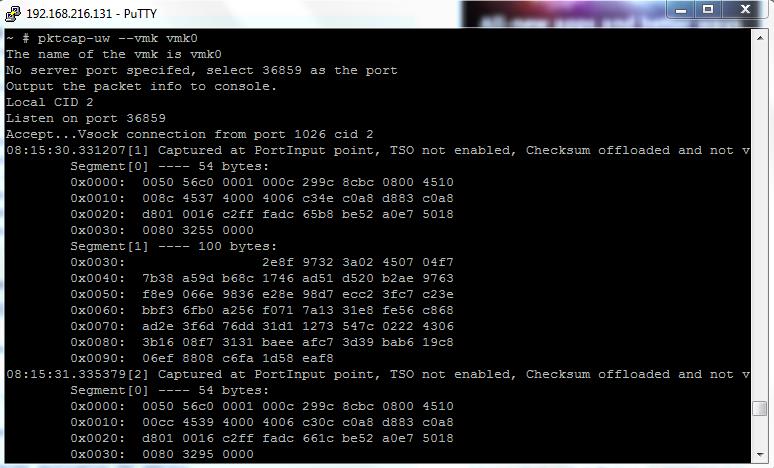
To View the live Capture of VMKernel Interface Traffic
pktcap-uw –vmk vmk0
Save the Capture to a output file:
To capture the output to a file, use -o option:
pktcap-uw –vmk vmk0 -o /tmp/vmk0capture.pcap
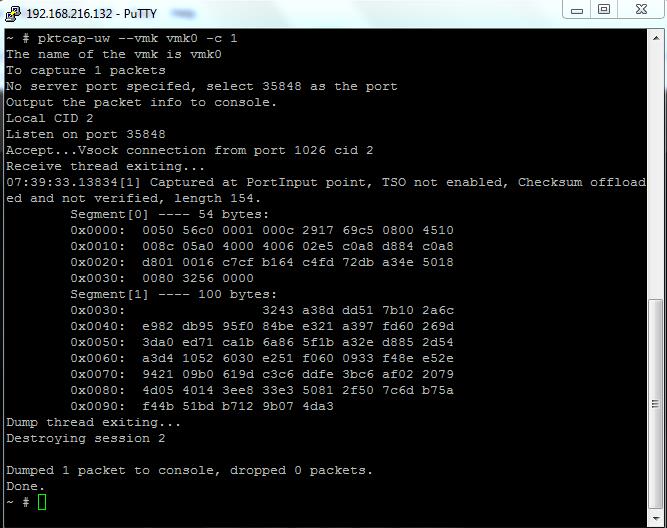
To limit the data being captured
you can limit the data being captured using the ‘-c’ option, which allows you to specify the number of packets you wish to capture
pktcap-uw –vmk vmk0 -c 1
Capture Traffic of a specific physical network card(vmnic) on ESXi Host:
pktcap-uw –uplink vmnic0
Capture traffic from a virtual switchport on a dvSwitch:
pktcap-uw –switchport switchportnumber
Ex, pktcap-uw –switchport 33554433
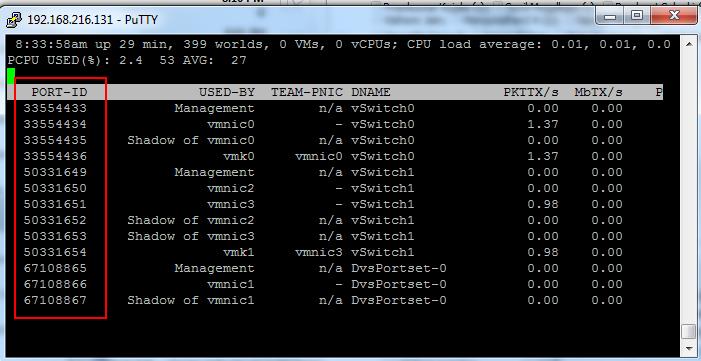
To get the Switch port ID
esxtop -> Press n -> PORT-ID
To Capture packets for multiple points simultaneously
Capture Packets of both Switch port and physical adapter at same time using the below command
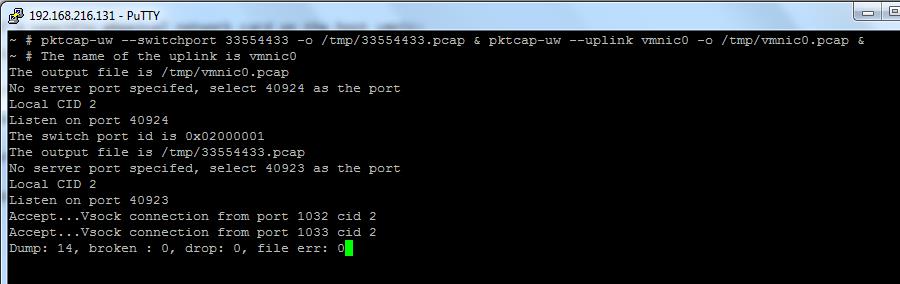
pktcap-uw –switchport 33554433 -o /tmp/33554433.pcap & pktcap-uw –uplink vmnic0 -o /tmp/vmnic0.pcap &
Stop pktcap-uw tracing with the kill command:
kill $(lsof |grep pktcap-uw |awk ‘{print $1}’| sort -u)
To check that all pktcap-uw traces are stopped:
lsof |grep pktcap-uw |awk ‘{print $1}’| sort -u
Captured packets can be viewed in Sniffer tools such as Wireshark.